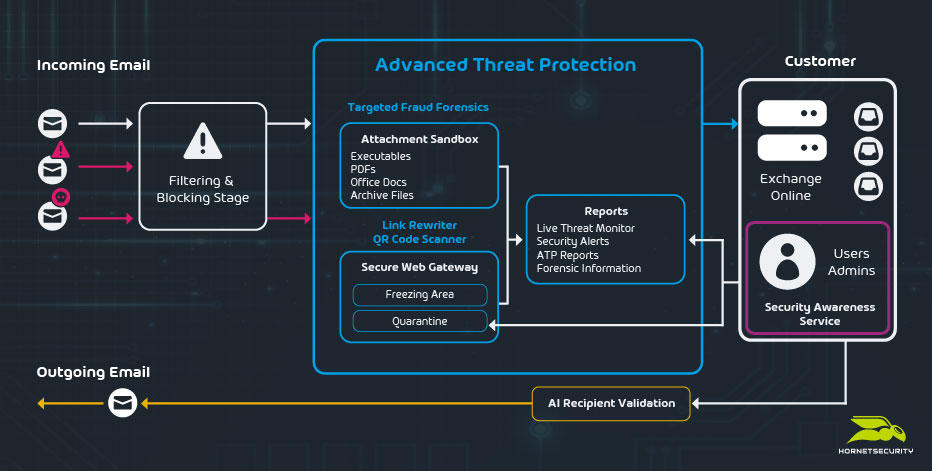
The above services deal with most of the incoming undesirable and malicious emails. However, attackers spend a lot of time and effort changing their attack methods to bypass email filters. This is where ATP comes in.
One popular option is attaching an encrypted document to an email. Normally anti-malware engines can’t scan these and so might miss a malicious file, ATP uses Malicious Document Decryption to protect against this.
QR codes in emails is an attack type that’s gained momentum in the last few months, partly because QR codes are now such a normal part of life (restaurant menus, paying for car parking etc.), and partly because it moves the attack from the (often) corporate owned and managed PC to a user’s personal phone.
It neatly bypasses all the protections in place on the computer and the URL in the QR code often leads to a familiar looking login page. ATP has had built in QR code scanning for common file types (GIF, JPEG, PNG and BMP) for over a year.
ATP has many layers of protection such as the Sandbox Engine, which will open all attached files, identifying malicious attachments and if they are, the email is quarantined.
The Sandbox Engine looks at if the attached files show signs of detecting that they’re running in a VM or a sandbox, which is a dead giveaway that it’s malicious. It also uses a file system monitor to see if the attachment writes or alter files, a process monitor to see if the file starts a child process (popular in malicious Adobe PDF files).
There’s also a registry monitor to spot unusual values being stored in the registry (often used for persistence when the PC is restarted) and network monitoring to see if the document is trying to communicate with an endpoint on the internet, another unusual behavior for a document.
Memory is inspected from a forensic point of view (again, documents accessing memory in unusual ways is a strong indication that it’s malicious). Tying it all together is a Machine Learning engine that looks at the above signals, and over 500 indicators, and separates malicious files from benign ones with very high accuracy.
Freezing is another approach, if an email is suspicious, but not clearly classified as bad yet, it’s held back for a short time. New data may lead to a positive identification of a virus attachment for example.
All links in emails (URLs) are rewritten with a link to our secure web gateway, and scanned both when the email is received and when the user eventually clicks on it.
To work around this, attackers often include the links in attached files, which can’t be rewritten (it would alter the integrity of the document), but our engine still follows these links to verify if there’s any malicious payload on the target end.
One very important feature of cyber security tools is to let you know when bad things are afoot, and ATP provides real-time alerts when your organization is under a targeted email attack.
A related feature is Ex-Post alerts: if emails that have already been delivered are subsequently identified as malicious your IT team is notified.
As mentioned, these emails can be automatically deleted, but the user may already have clicked a link, or opened an attachment, so your response team might want to investigate these user accounts / devices further.
Human beings are still the weakest link, and our psychology is used against us when attackers employ social engineering tactics.
Our Targeted Fraud Forensics uses automated fraud attempt analysis and intention spoofing recognition to detect and prevent social engineering attacks.
It looks at the language of the email, looking for patterns that indicate malicious intent, espionage attacks, or if the text presents false facts to get the recipient to respond, as well as spotting forged sender identities.

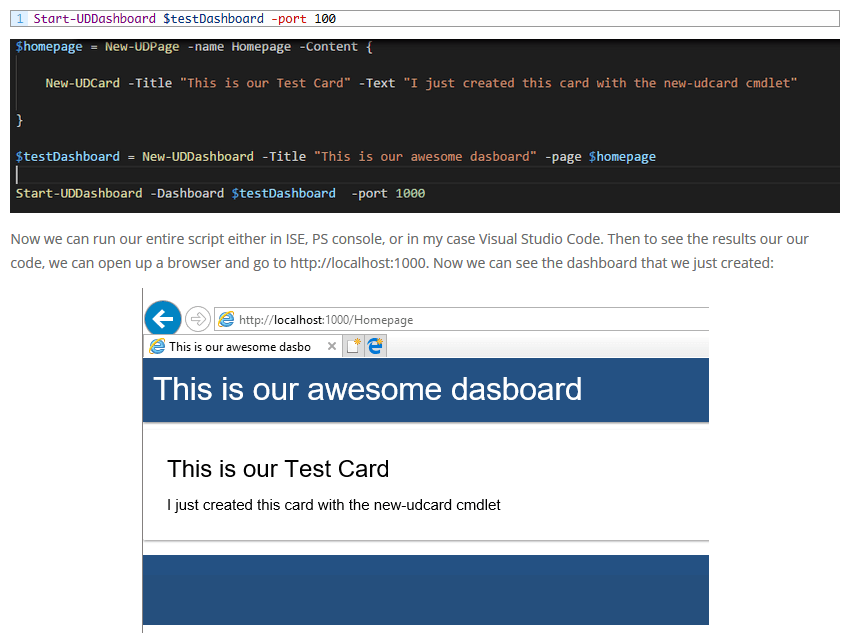


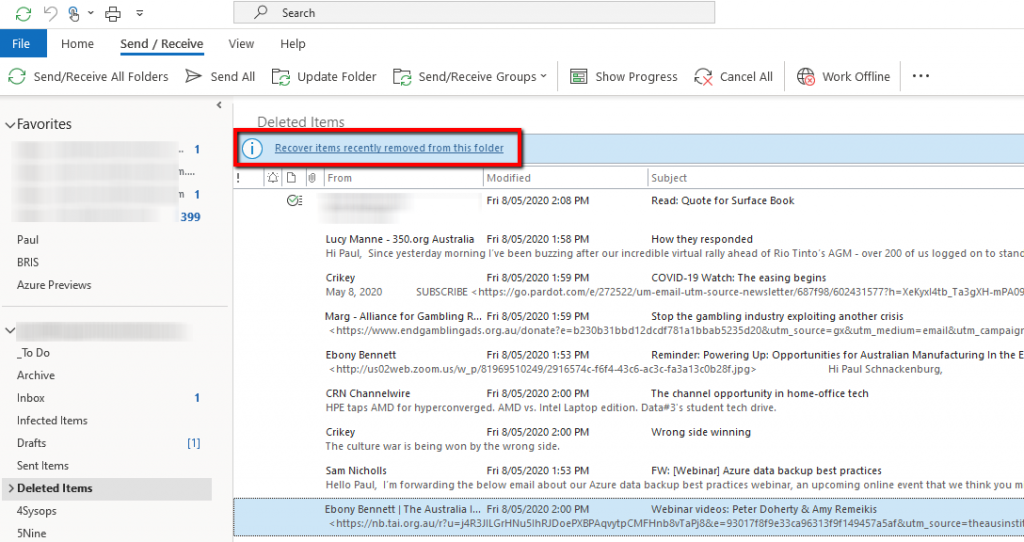
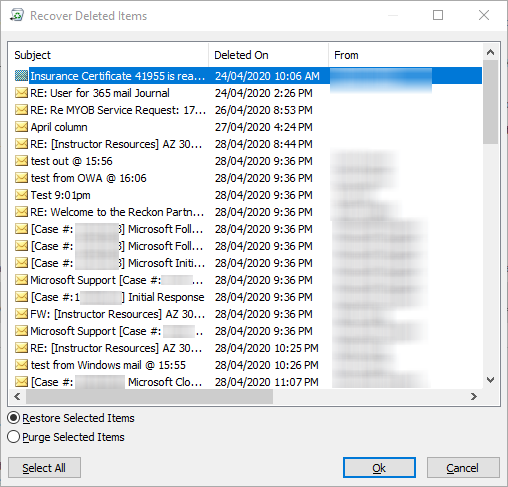
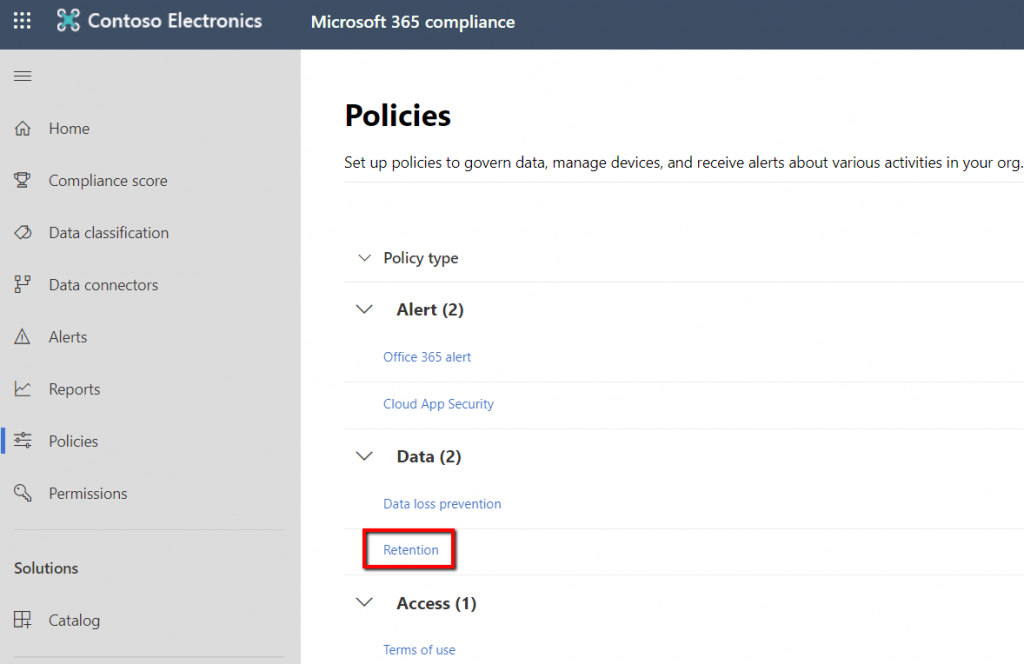
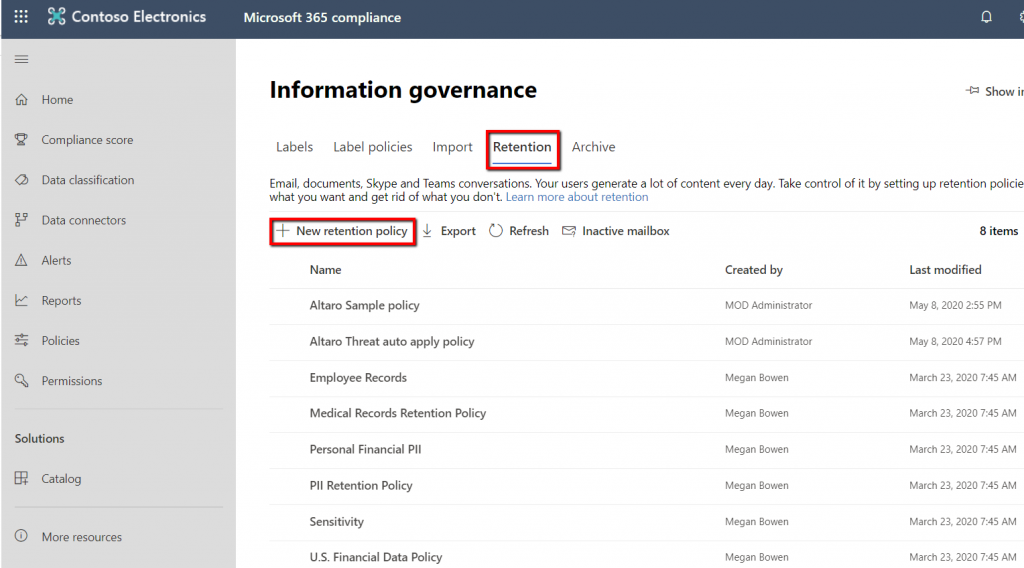
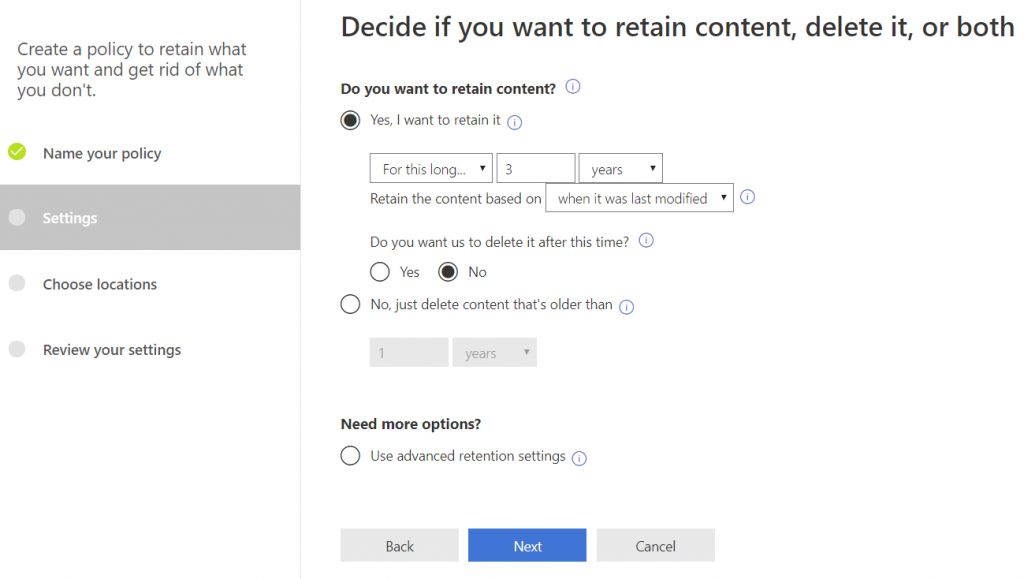
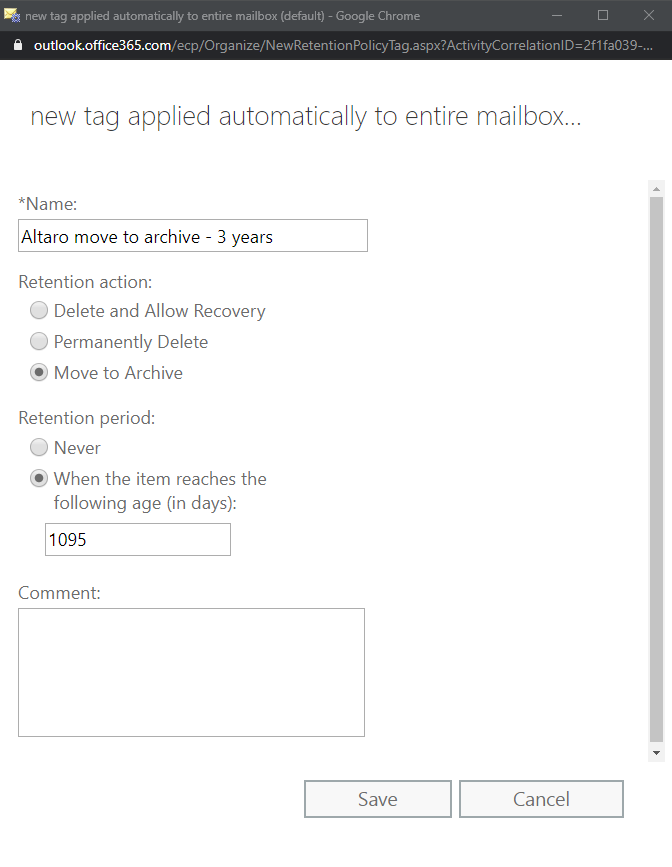


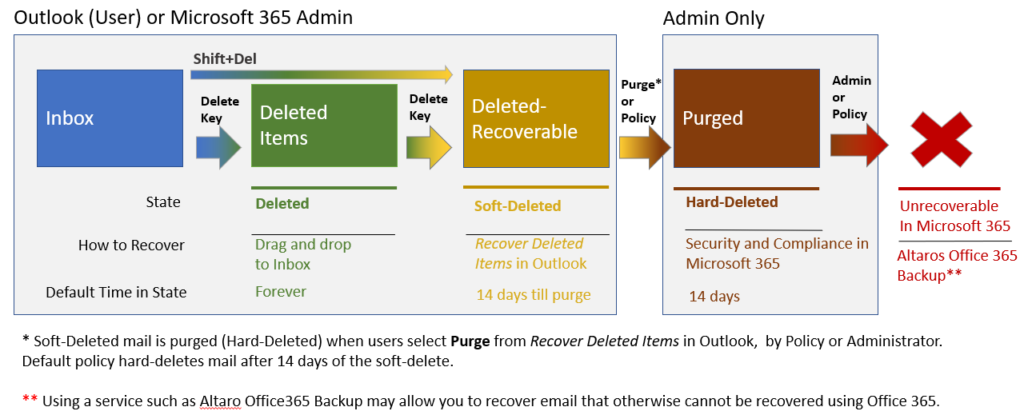
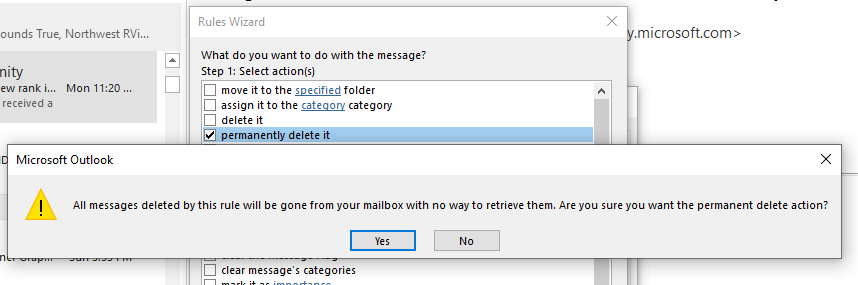
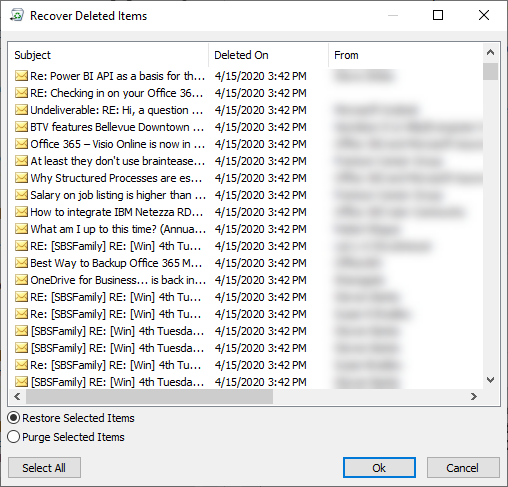
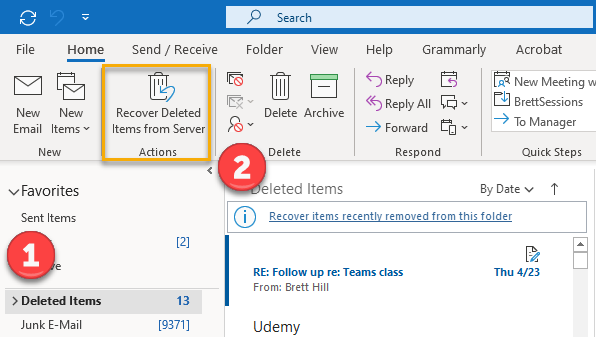 Clicking on the recover items link opens the Recover Deleted Items window.
Clicking on the recover items link opens the Recover Deleted Items window.